
ТОР 5 статей:
Методические подходы к анализу финансового состояния предприятия
Проблема периодизации русской литературы ХХ века. Краткая характеристика второй половины ХХ века
Характеристика шлифовальных кругов и ее маркировка
Служебные части речи. Предлог. Союз. Частицы
КАТЕГОРИИ:
- Археология
- Архитектура
- Астрономия
- Аудит
- Биология
- Ботаника
- Бухгалтерский учёт
- Войное дело
- Генетика
- География
- Геология
- Дизайн
- Искусство
- История
- Кино
- Кулинария
- Культура
- Литература
- Математика
- Медицина
- Металлургия
- Мифология
- Музыка
- Психология
- Религия
- Спорт
- Строительство
- Техника
- Транспорт
- Туризм
- Усадьба
- Физика
- Фотография
- Химия
- Экология
- Электричество
- Электроника
- Энергетика
SoftselUK(081)568-8866 PAP (0706) 217-744
Ingram Micro UK (0908) 260-160 Frontline (0256) 27880

|
XTREE
 82
82
FREE FACTS O91
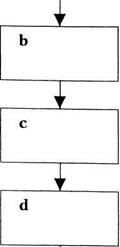
The flowchart on the following page represents the steps in the process by
,,,.^vnr;-<>ry..> ■ ■:-iir--'..-. - " PU: Mh- \ • ■ •■ ■■ ■
advertisement, match each step with the corresponding letier in the llowchart.
I

|
|

|

|

|
1 Virus signature database is updated.
2 Is virus known?
3 AllSafe scans other disks or systems in order to prevent further infection immediately.
4 AllSafe searches for indications that viruses are attempting to copy themselves.
5 AllSafe identifies and isolates the virus.
6 AllSafe eliminates the known virus.
7 AllSafe analyses the virus and learns its signature straight away.
 Find words or phrases in the text which mean:
Find words or phrases in the text which mean:
1 wickedness, badness, danger
2 hides (while waiting to attack)
3 causing a lot of damage
4 people who interfere without authorization
5 terrify, make very afraid
6 combines
7 identified, recognized
8 frightening
9 choices
10 attackers
Speaking
Discuss the following questions:
1 What technique does the advertisement use to persuade people to buy the
product?
2 Do you think the advertisement is successful? Give reasons for your opinion.
3 What other techniques could be used to sell this kind of software?
 Task 15
Task 15
Writing
Design an advertisement for a PC protection package. Your advertisement should mention all the features listed below, but you may add others. Choose a i, and decide on the best way to present your product.
Features
Password protection - system manager controls what each user is permitted to
do
Fill* encryption - plain text messages are converted into cipher (code) so that
only authorized recipients can read them
Keyboard lock - screen is cleared and keyboard is locked after pre-set period of
inactivity
Task 16
Reading
Roiul this news report and discuss the questions that follow.
 NSA consultant's son is computer saboteur
NSA consultant's son is computer saboteur
'Worm' camefrom graduate student

|
| A |
court heard today how a Cornell. University graduate student, Robert T. Morris Jr. (25), infected a host of government and educational computer centres with a computer virus, known as a 'worm', which literally brought all computational activity to a halt in over 6,000 installations. Morris, the son of a prominent National Security Agency computer consultant, was sentenced for his offences yesterday. As punishment, he was required to spend no time in prison but, instead, serve three years' probation, contribute 400 hours of community service, and to pay a $10,000 fine along with associated court and probation costs.
Wcw serious do you think Robert Morris's crime was?
IV you think the punishment was
a too severe?
b about right?
c not severe enough?
Do you know of any similar incidents of computer hacking?
Task 17
Word-play
The words and phrases below are taken from this unit. In pairs or groups. decide if they have a 'protective' or a 'destructive' meaning as they are used in the unit, then put them under the correct heading.
| detonator | infcctor | erase | pirated |
| infect | write-protect tab | worm | virus scanner |
| hacker | password | smart card | shield |
| signature | cipher | keyboard lock | access control |
| protective | destructive |










 How many other ways can you think of to classify them?
How many other ways can you think of to classify them?
Language focus G
Listing
It is important when reading to recognize and understand the relationship in which sentences and groups of sentences combine to present information. This information may be linked by means of a connective word or marker.
Making a list, for example when enumerating, and giving instructions, indicates a cataloguing of what is being said. It is important to note that most enumerations belong to clearly defined sets. The following table is a list of the markers that can be used to show the order in which things are to be said.
L
I
L I
I I 1 1 I I
 1,2, 3, etc.
1,2, 3, etc.
one, two, three, etc.
first(ly), second(ly), third place
another, next, then
furthermore, afterwards, moreover
lastly/finally
to begin/start with, and to conclude
I;

 first and foremost
first and foremost
first and most important(ly)
mark the beginning of a descending order
above all
last but not least
mark the end of an ascending order
 There are many ways of showing sequential relationships. Those given in the table above are not the only ones, they are the most common ones used in listing or enumerating. The Ay forms are usually used when listing.
There are many ways of showing sequential relationships. Those given in the table above are not the only ones, they are the most common ones used in listing or enumerating. The Ay forms are usually used when listing.
Sample paragraphs:
More and more police departments are now using sophisticated devices to help rontro] the increasing crime rate. Some of these devices are: firstly, a computer terminal inside a police vehicle to answer an officer's questions, secondly, a computer-controlled display unit for displaying fingerprints, and thirdly, educational systems for police officers such as terminals, enabling them to verify changes in laws, rules, and regulations.
The computer memory of many law enforcement systems contains all kinds of information. First and foremost, it has data on stolen items such as cars, licence plates, and property. Second, it has information on missing persons and wanted fugitives. Last but not least, it contains information on political extremist groups and their activities.
I:
r
c
I—
R"
» f
i
Exercise 1
 Exercise 2
Exercise 2
Computers have certainly revolutionized police work by providing access to millions of items of information with the least possible delay and speeding up the process of apprehending suspicious-looking characters.
Complete the following paragraph about the various steps in the creation of a database by filling in the blanks with appropriate listing markers.
When you are creating a new database, you must!________________________ decide how
many fields you will need in your database. [... __________________, you will have to
provide up to five items of information about each field.!_______________________ _, each
field needs to have a name__________________, the field type has to be defined.
Character, numeric, date, and logical are some common types._____________________..
choice to be made is the width of the field. However, some fields, such as date,
have present default values. The___________________ step is to set the number of
decimal places if the field is numeric.!___________________, you will have to indicate
whether the field is to be indexed or not.
Complete the following paragraph by filling in the blanks with appropriate listing markers.
Computers can do wonders, but they can waste a lot of money unless careful consideration goes into buying them. Businessmen and women thinking of
buying a computer system should____________________ admit they know very little
about computers-------------------, they must realize that the computer sales
people don't always know how their business works.
_____________, it is essential that buyers should get outside advice, not
necessarily from consultants but from other executives who have had recent
experience in buying a computer system..
they should try to see
| 8 7 |
systems similar to ones under consideration in operation. Because their operations will have differences that must be accommodated, they should
_____________ find out what would be involved in upgrading a system.
_____________ important thing to know before buying a computer is the
financial situation of the supplier because computer companies come and go
and not all are financially stable. I___________________, the prospective buyer should
demand that every detail be covered in writing, including hardware and software if they are supplied by different companies. There's nothing wrong with computers themselves, it's how and why they are used that can cause problems.

|
Не нашли, что искали? Воспользуйтесь поиском: